Cyber defenses ramp up as hacks exploit gaps
Reprints
Organizations continue to race against cybercriminals to keep their systems secure by focusing on defensive measures, including addressing supply chain weaknesses, removing software vulnerabilities and exploring alternatives to traditional passwords.
Ransomware remains the predominant attack approach they face. Last year’s record number of ransomware attacks included a 67% year-over-year increase in fourth quarter incidents, according to a recent report by Corvus Insurance Holdings Inc.
Experts are also concerned about criminals’ use of generative artificial intelligence, although it can also be effectively used by companies as a defense (see related story).
Cybersecurity is simultaneously fast and slow moving, said Chester Wisniewski, Vancouver, British Columbia-based director, field chief technology officer, for cybersecurity company Sophos Ltd.
 Criminals and nation states are innovating incredibly quickly, Mr. Wisniewski said. “There’s a pace of innovation among those profiting from stealing information that makes it harder for businesses to keep on top of,” he said.
Criminals and nation states are innovating incredibly quickly, Mr. Wisniewski said. “There’s a pace of innovation among those profiting from stealing information that makes it harder for businesses to keep on top of,” he said.
Meanwhile, security efforts are held back by long-standing issues, such as reusing passwords and failing to keep patches up to date, he said.
“We keep forgetting that all the bad guys really need is one little gap” to enter systems, said Ed Dubrovsky, Toronto-based chief operating officer and a partner at Cypfer Inc., a cybersecurity company.
The average ransomware model “hasn’t changed very much” said Mark Stockley, Oxford, England-based cybersecurity evangelist for Malwarebytes, a cybersecurity company. “We still see criminals sending out malware in waves of email,” some of which will get through.
While traditional ransomware “is still very much a thing,” it tends to be used to target small and medium-sized enterprises, said John Dwyer, Pittsburgh-based head of research at IBM Security X-Force, a security division of IBM.
In attacking larger companies, criminals often buy readily available company data through the dark web that they threaten to release, he said.
Ryan Witt, Sunnyvale, California-based vice president of industry solutions for Proofpoint Inc., a cybersecurity company, said that while ransomware gets a lot of attention, “there’s way more money lost” by companies to broad-based attacks — where payments are redirected, data pilfered or credentials stolen — that permit criminals to navigate networks and determine what to attack or exploit.
An ongoing concern is third-party suppliers. In response to companies’ introduction of more rigorous firewalls and employment management systems, criminals have used suppliers as a way into their computer systems, said Eric Byres, CEO of Victoria, British Columbia-based aDolus Technology Inc.
He pointed to SolarWinds Corp. software which, beginning in 2019, was used in cyberattacks perpetrated by the Russian Foreign Intelligence Service to deploy malicious code into the computers of thousands of companies and government agencies worldwide.
“A zero-trust network is one of the ways to help manage that risk,” Mr. Wisniewski said. Such protocols require identity verification for every person and device trying to access a private network, and limiting even legitimate third parties to specific areas of the network.
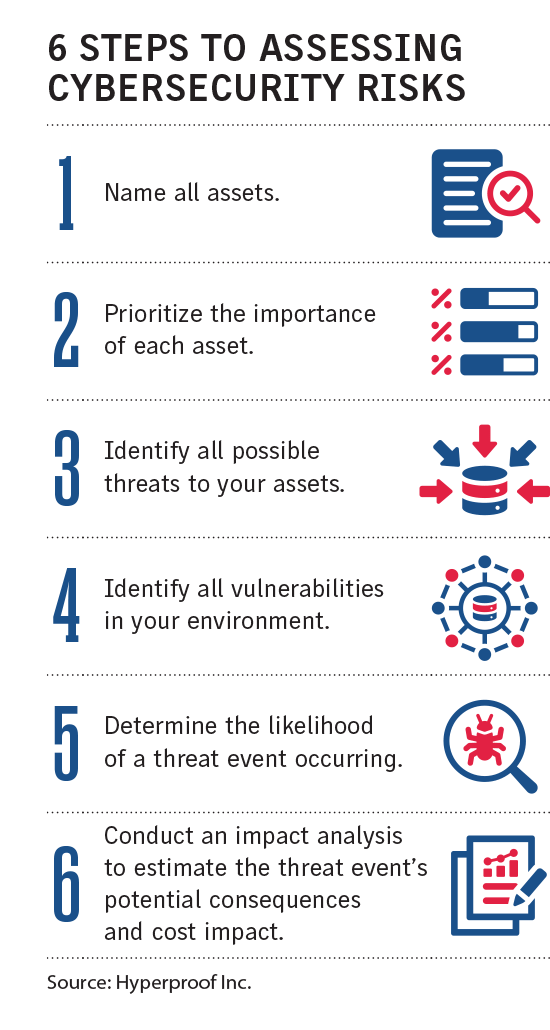 Corporate software may also be a problem, experts say.
Corporate software may also be a problem, experts say.
Complex software packages usually include open-source software with a source code that anyone can modify and whose vulnerabilities may be unknown even to the vendors that sell them.
In December 2021, for instance, a critical vulnerability was found in Log4J, a widely used open-source software.
According to Synopsys Inc.’s 2023 Open Source Security and Risk Report, 84% of codebases have at least one known open-source vulnerability, and 48% contain high-risk vulnerabilities.
One approach to dealing with the issue is to compile a software bill of materials, a list of all the opensource and third-party components present in a codebase, experts say. President Biden signed an executive order requiring SBOM’s use by the federal government in 2021.
This approach, though, is in its early stages of development. “It’s not there yet,” said Rani Osnat, Tel Aviv-based senior vice president, strategy and business development, for Aqua Security Software Ltd. It still “doesn’t necessarily go all the way to the base level,” he said.
And companies should prioritize their security concerns, said Andreas Kroier, Vienna-based senior principal, solution lead of application security, at software company Dynatrace Inc.
In analyzing software, it is important to distinguish the exposures that need to be fixed first from those that are relatively harmless and sit “in back of the environment” to avoid “chasing phantom problems,” he said.
Companies are also moving away from traditional passwords, which are vulnerable to cybercriminals, and toward using cell phones or biometric devices that may require a fingerprint or facial ID and multifactor authentication.
“I would love to see the password die,” Mr. Wisniewski said. “It is a leading way organizations are compromised.”