SEC toughening cyber enforcement
Posted On: Oct. 5, 2021 12:00 AM CSTThe U.S. Securities and Exchange Commission will continue to pursue companies that breach securities laws by making inadequate cybersecurity disclosures, experts say.
“They have made that clear,” said Alexander H. Southwell, a partner with Gibson Dunn & Crutcher LLP in New York, who co-chairs the firm’s privacy, cybersecurity and data innovation practice group.
To avoid SEC actions, experts advise that companies establish clear internal communications strategies to address the issue.
Observers say the SEC’s recent activity is part of a broader administrative response to the issue.
Tom Finan, director, cyber practice, for Willis Towers Watson PLC in Washington, said, “Obviously, the SEC is increasingly focusing on this topic of cybersecurity disclosure. I think it has a lot to do with the whole government approach that we’re seeing play out in live action.”
He pointed to the White House meeting on cybersecurity in August that insurance executive attendees said was productive and left them more optimistic about businesses’ ability to tackle the issue.
Cybersecurity has become a high priority for federal agencies, and “the SEC is obviously using its tools to bring that home to publicly traded companies,” he said.
The agency’s enforcement actions “show us that the SEC is out of patience with companies that fail to implement the kind of internal controls that would allow a company to be accurate in its disclosures,” said Priya Cherian Huskins, San Francisco-based partner and senior vice president at broker Woodruff-Sawyer & Co.
The agency will likely become even more aggressive in the future, said John Farley, New York-based managing director of Arthur J. Gallagher & Co.’s cyber liability practice. “As time goes on, the SEC is going to have less tolerance for organizations that don’t take the basic steps to protect sensitive data,” he said.
“The implication is, companies need to take a whole enterprise approach” and have a “powerful cybersecurity story that explains how they are viewing risks and aligning their resources to address those risks and how they are planning for the future,” Mr. Finan said.
“At a general level, cyber risks have become a focal point for all companies,” said Matthew McLellan, Marsh LLC’s Washington-based U.S. D&O practice leader.
The issue has clearly had an effect across different business sectors, and companies have been ramping up their cyber controls and internal risk management systems, as well as their disclosure procedures for communicating with investors, he said.
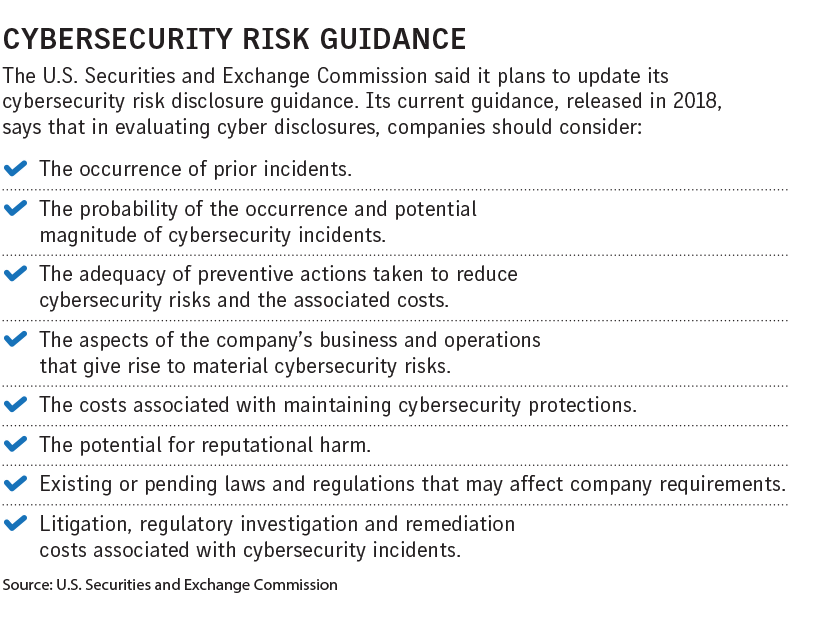
The SEC issued guidance on cybersecurity disclosures in 2018, and an update is expected, experts say, pointing out it was among the items included in its Spring 2021 Unified Agenda of Regulatory and Deregulatory Actions issued in June.
“I would expect there will be some new guidance,” Mr. Southwell said.
Companies should develop incident response plans that include how to deal with a vulnerability’s discovery before it becomes an intrusion, then make sure the infrastructure is in place to address that vulnerability, Mr. McLellan said.
Tamara D. Bruno, a partner with Pillsbury Winthrop Shaw Pittman LLP’s insurance recovery practice in Houston, said companies should make sure they “fully understand their own cybersecurity environment.” This means communicating regularly with staff who can bridge communication gaps between those who implement cybersecurity and those who handle disclosures.
“Essentially, it boils down to companies needing to know what is mission critical to their organizations” and preventing a cyber event that will shut them down, Mr. Finan said.
If there is a cyber incident, companies should be careful about their disclosures and make sure they are comprehensive, said Thomas O. Gorman, a partner at Dorsey & Whitney LLP in Washington.
A well-constructed directors and officers policy should cover investigation costs, said William Boeck, senior vice president, U.S. financial lines claims practice leader and global cyber product and claims leader for Lockton Cos. LLC in Kansas City, Missouri. It is unlikely that the coverage will extend to fines and penalties, although there are some specialized products available that may do so, he said.
A cyber liability policy could respond to an SEC investigation, depending on its wording, “but there’s a big caveat to that, and that is that cyber policies typically exclude non-privacy-related fines,” he said.
Most cyber policies also have exclusions for security-related claims, which may become an issue if there are more SEC enforcement actions, Mr. Boeck said.
Firms pay penalties for inadequate disclosures
The U.S. Securities and Exchange Commission has announced two settlements related to cybersecurity disclosures and has sought voluntary information in its investigation of the SolarWinds Corp. cyberattack.
On June 15, without admitting or denying the SEC’s findings, Santa Ana, California-based First American Financial Corp., a title insurance services company, agreed to pay a $487,616 penalty for allegedly failing to disclose a cybersecurity vulnerability.
In May 2019, the company learned its application for sharing document images had a vulnerability that exposed more than 800 million images dating back to 2003, including personal data, the SEC said. The company then issued a press statement and a Form 8-K.
However, the agency said the senior executives responsible for those public statements were not informed that the company’s information security personnel had identified the vulnerability several months earlier but had failed to remediate it in accordance with the company’s policies.
On June 21, the SEC said London-based educational publishing company Pearson PLC had agreed to pay $1 million to settle charges that it misled investors about a 2018 intrusion.
The SEC said Pearson made misleading comments and omissions regarding a 2018 data breach involving the theft of student data and administrator log-in credentials of 13,000 school, district and university customer accounts.
In June, the SEC said it was launching an investigation into the December 2020 SolarWinds cyberattack and was seeking voluntary information from those who may have been impacted.
The SEC said its enforcement division would not recommend enforcement action against companies that voluntarily provided the information requested in the letter.